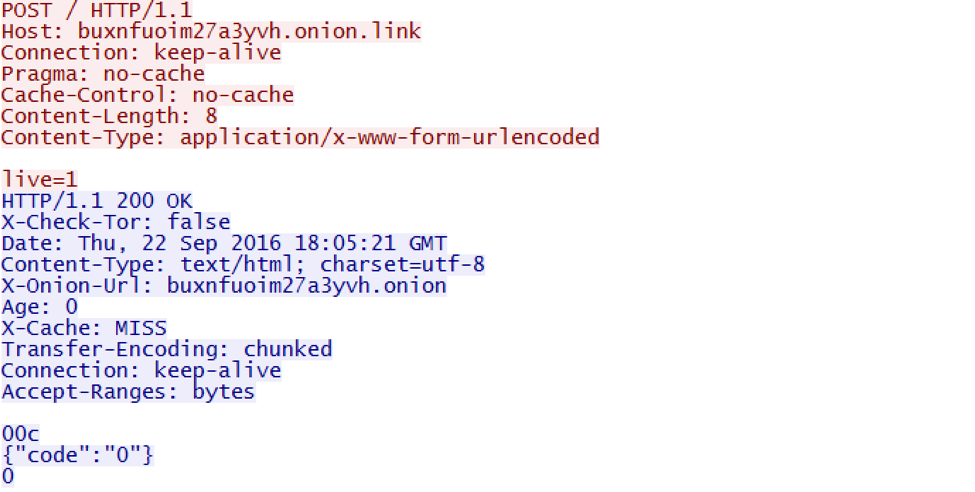
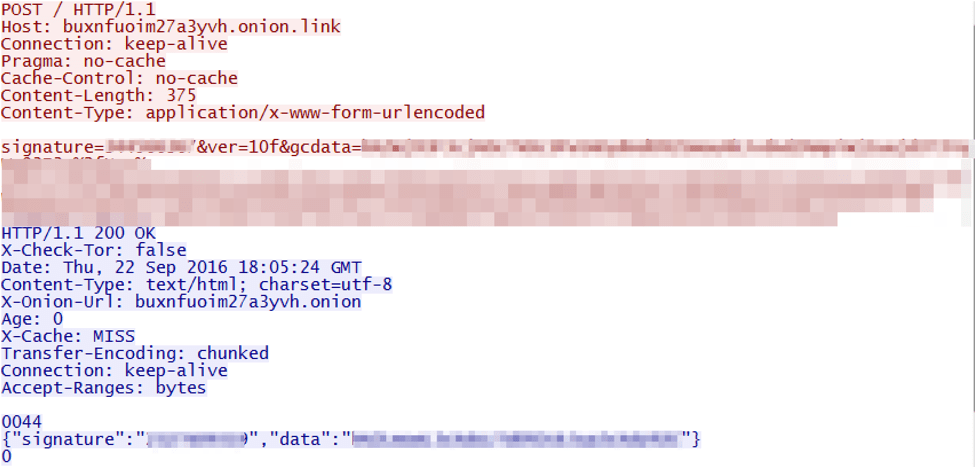
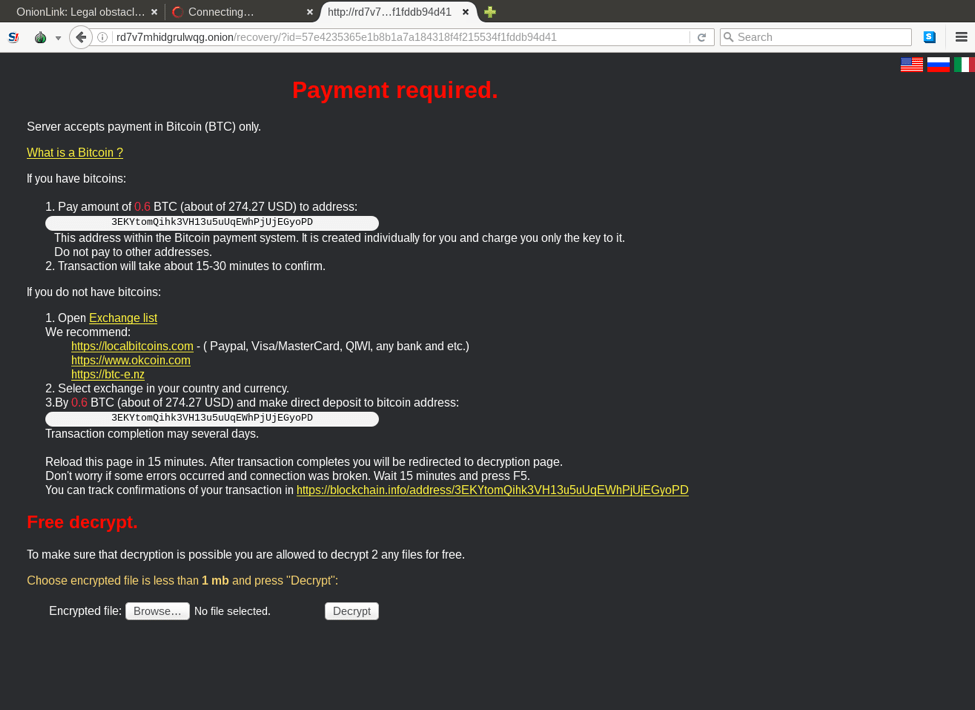
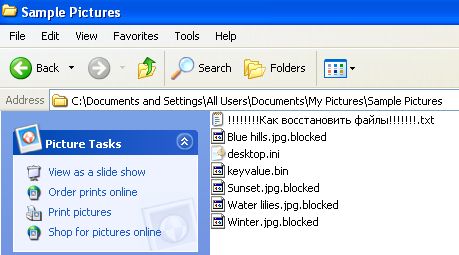
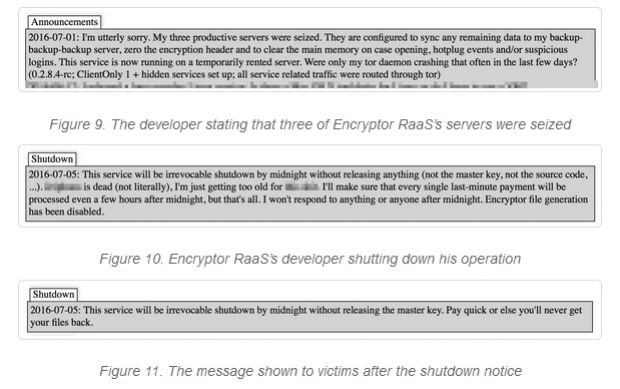
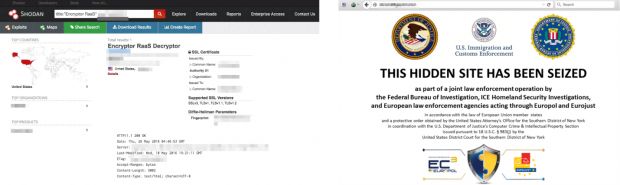
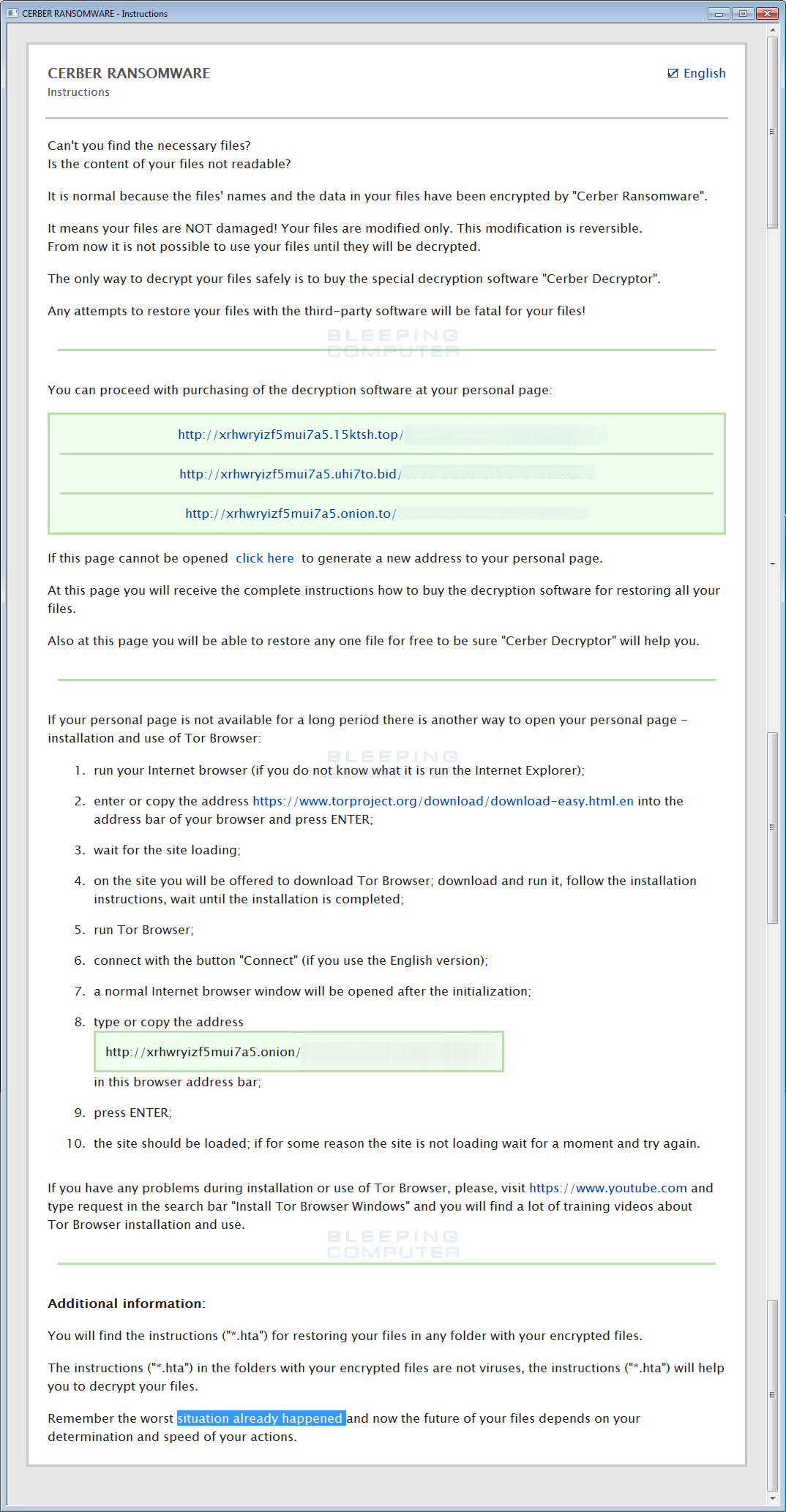
According to the popular cyber security experts an unknown nation state actor may be running tests for taking down the entire internet infrastructure. What happens if someone shuts down the Internet? Is it possible?
Our society heavily depends on technology and the Internet is the privileged vector of the information today. Blocking the Internet could paralyze countless services in almost any industry, from finance to transportation.
Early September the popular cyber security expert Bruce Schneier published an interesting post titled “Someone Is Learning How to Take Down the Internet” that reveals an escalation of cyber attacks against service providers and companies responsible for the basic infrastructure of the Internet.
We are referring to coordinated attacks that experts consider a sort of tests to evaluate the resilience of most critical nodes of the global Internet. The attacks experienced by the companies request a significant effort and huge resources, a circumstance that suggests the involvement of a persistent attacker like a government, and China is the first suspect.
“Recently, some of the major companies that provide the basic infrastructure that makes the Internet work have seen an increase in DDoS attacks against them. Moreover, they have seen a certain profile of attacks. These attacks are significantly larger than the ones they’re used to seeing. They last longer. They’re more sophisticated. And they look like probing.” wrote Schneier.
“I am unable to give details, because these companies spoke with me under a condition of anonymity. But this all is consistent with what Verisign is reporting. Verisign is the registrar for many popular top-level Internet domains, like .com and .net. If it goes down, there’s a global blackout of all websites and e-mail addresses in the most common top-level domains. Every quarter, Verisign publishes a DDoS trends report. While its publication doesn’t have the level of detail I heard from the companies I spoke with, the trends are the same: “in Q2 2016, attacks continued to become more frequent, persistent, and complex.”
It is clear that attackers aim to cause a global blackout of the most common top-level domains paralyzing a large portion of the Internet.
Schneier, who has spoken with companies that faced the attacks, pointed out powerful DDoS attacks that attacks that stand out of the ordinary for their methodically escalating nature.
The attacks start with a certain power that increases as time goes by forcing the victims to deploy all its countermeasures to mitigate the threat.
The report mentioned by Schneier, titled “VERISIGN-OBSERVED DDoS ATTACK TRENDS: Q2 2016” confirms that companies are experiencing a wave of DDoS attacks even more sophisticated.

“DDoS Attacks Become More Sophisticated and Persistent DDoS attacks are a reality for today’s web-reliant organizations. In Q2 2016, DDoS attacks continued to become more frequent, persistent and complex.” states the report.
Schneier also reported other types of attacks against the Internet infrastructure, such as numerous attempts to tamper with Internet addresses and routing.
“One company told me about a variety of probing attacks in addition to the DDoS attacks: testing the ability to manipulate Internet addresses and routes, seeing how long it takes the defenders to respond, and so on. Someone is extensively testing the core defensive capabilities of the companies that provide critical Internet services.” continues Schneier.
Who is behind the attacks?
Schneier believes that the attacks are launched by someone with cyber capabilities of a government, and he seems to exclude the efforts of hacktivists or cyber criminals, and I agree.
“It doesn’t seem like something an activist, criminal, or researcher would do. Profiling core infrastructure is common practice in espionage and intelligence gathering. It’s not normal for companies to do that. Furthermore, the size and scale of these probes — and especially their persistence — points to state actors.” explains Schneier.
The attribution of the attacks is very difficult by data suggests that China is behind them, let me add also that Russia has similar cyber abilities and is able to hide its operations online. Both countries are largely investing in building infrastructures that would be resilient to such kind of mass attacks.
Source:http://securityaffairs.co
The post A nation-state actor is testing methods for a massive takedown of the Internet appeared first on Information Security Newspaper.